you@chainsawcannon:/Blog/Industrial_Control_Fundamentals/Disclaimer$
Synopsis/Disclaimer
The following blogpost is archived from my spacehey, which is a lecture from Schweitzer Engineering Laboratories. This lecture took place last year (4/21/2023 estimated). This blogpost was published with permission from Schweitzer Engineering Laboratories as well.
I would also like to include a trigger warning since this blog subtly mentions death from an incident in cybersecurity, if you are easily triggered please avoid the section:Need for ICS Security. Thank you for reading and stay tuned for the rest of the parts (which also may be revised compared to their spacehey counterparts)
you@chainsawcannon:/Blog/Industrial_Control_Fundamentals$
Introduction to ICS
ICS operate industrial plant equipment and critical processes, which include supervisory control and data acquisition (SCADA), Distributed Control Systems (DCS), Programmable Logic Controllers (PLC), etc. Control systems have four functions: Measuring, Comparing, Computing, and providing corrective calculations. Functions are performed by five elements: Sensors, Transducers, Transmitters, Controllers, and control elements.
The main groups of ICS components are field devices(Meters, Sensors, Switches, Valves), field controllers(Controllers, IEDs, PLCs, RTUs), and HMI's (HMIs, SCADA servers, Workstations). Field devices to field controller- field protocol. Field controller to HMI, command and control.
Operational Technology are programmable systems or devices that interact with the physical environment that detect or cause a direct change through the monitoring and/or control of devices, processes, and events. (Industrial Control Systems, Building management systems, fire control systems, physical access control mechanisms.)
Definitions:
SCADA- Supervisory Control and Data Acquisition- Used to control dispersed assets where centralized data acquisition is as important as control. - Integrates data acquisition systems with data transmissions systems and human-to-machine interfaces (HMI) Software.
HMI- Human Machine Interfaces- The hardware or software through which an operator interacts with a controller. This can range from physical control panels with buttons and indicator lights to an industrial PC with a color graphics display running dedicated HMI software!
PLC - Programmable Logic Controller- An industrial computer originally designed to perform the logic functions executed by electrical hardware (relays, switches, and mechanical timer/counters). These are capable of controlling SUPER complex processes , Substantially used in SCADA systems, DCS and almost ALL industrial processes. It is used as the primary controller in smaller system configurations.
RTU- Remote Terminal Unit- Special purpose data acquisition and control unit designed to support DCS and SCADA remote stations. These are often equipped with network capabilities which can include wired and wireless radio interfaces to communicate to a supervisory controller.
IED- Intelligent Electronic Devices- Any device incorporating one or more processors with the capability to receive or send data/control from or to an external source. (electronic multi-function meters, digital relays, and controllers).
OT Archetecture
Purdue Enterprise Reference Architecture:
- Level 4: Business Logistics Systems
- Level 3: Manufacturing Operations Systems
- Level 2: Control Systems
- Level 1: Intelligent devices
- Level 0: The Physical Processes
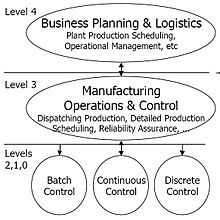
Implementing reference architectures - Reference architectures are specific to each situation depending on business functions and vary between vendors and industries, examples include oil-refinery system architecture. - you can use wireshark to look into these architectures as well.
The OT side is more behind compared to the IT side, which causes its flaws.
Power System Architecture:
- Level 5: Perimeter
- Level 4: SCADA
- Level 3: Access
- Level 2: Automation
- Level 1: Protection
- Level 0: Physical
IT vs OT
IT is focused on data and communication, whereas OT is focused on behaviors and outcomes.
IT (Office IT as example): Antivirus is commonly used, the component lifetime is 3-5 years, Outsourcing is common, Application of patches is regular and scheduled, Real time requirement delays are accepted, Security testing and audits are scheduled and mandated, Security Awareness is high and so is Physical security.
OT (Energy Control Systems as example): Antivirus is uncommon and hard to deploy, the component lifetime is up to 20 years, outsourcing is rarely used, application of patches are use case specific, real time requirement is critical due to safety, Security testing is rare due to operational networks, physical security varies a ton, and the security awareness is increasing.
Taking certain OT systems down cause major issues (Example: Florida Water system hack)
The CIA triad:
- Confidentiality: Keep organizations data private or secret.
- Integrity: Keep organizations data whole or complete
- Availability: Keep organizations networks, systems, and applications running smoothly
Practice Problem from lecture: "Which of the three factors of the triad is most important for OT vs IT?"
OT focuses more on Integrity and and IT focuses more on Confidentiality
Need for ICS Security
Energy is vital to critical infrastructure.
Practice Problem From Lecture: Why is it important to secure ICS network and devices?
Using the example of the water hack back then, it released deadly amounts of specific chemicals into the water which could have caused death to others. There is also hospitals and nuclear plants that DEPEND on ICS.
Why is ICS security critical?
Tampering can lead to: Death and injury, equipment damage, and more.
Attack Examples!!! :D
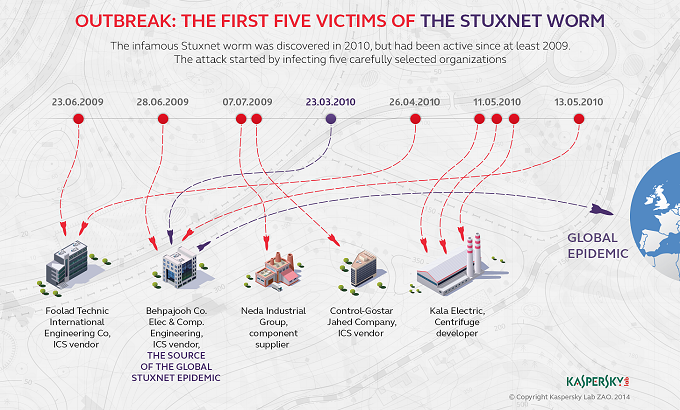
Stuxnet
PLC targeting worm that was identified in 2010, designed to destroy centrifuges Iran was using to enrich uranium.
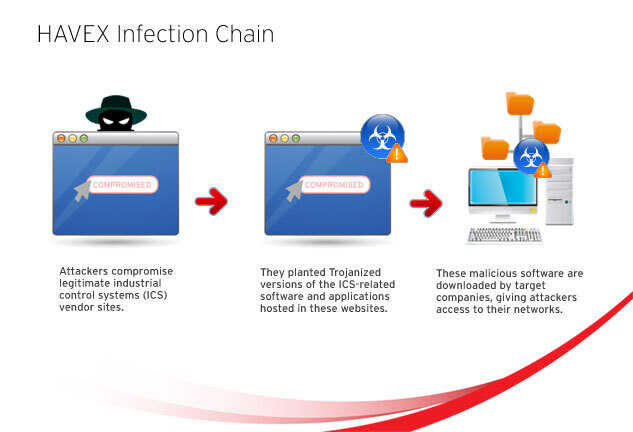
Havex
Remote Access Trojan and Command And Control malware. - Targeted OPC protoxol on popular SCADA/ICS ports
Crashoverride/Industroyer
Malware framework aimed at electrical substations.
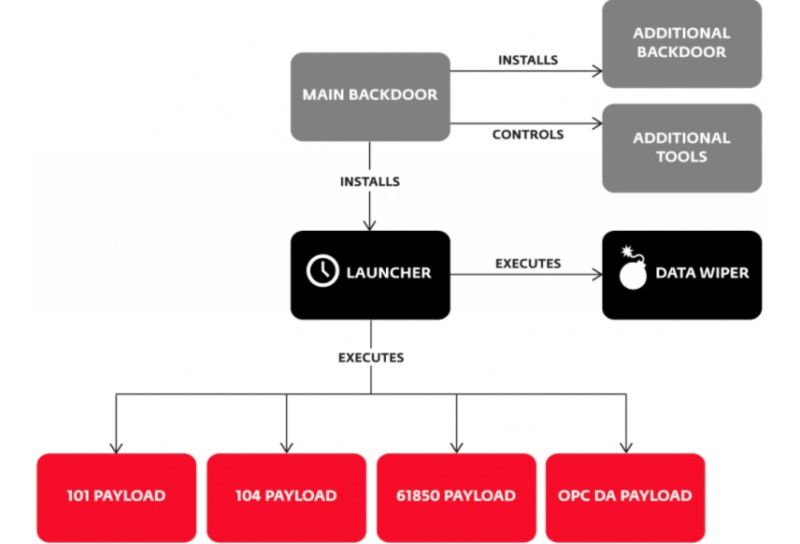
Pipedream
Toolkit disclosed in 2022 that targets PLCs and ICS
Anatomy of a Cyber Attack
Definition: An attack, via cyberspace, targeting an enterprises use of cyberspace for the purpose of disrupting, disabling, or destroying infrastructure.
Types of malicious actors: Identity theives (Tech Support/FBI scammers), Spammers or adware spreaders (Bonzi Buddy), Advanced Persistent Threats, Corporate Spies (Paid by other company to access other company), Hacktivists (Anonymous), Script Kiddies (I use Kali, I'm a haxxor now xD Also Discord QR code scammers), Traditional Hackers, Cyber Criminals, Normal Users ("Racecar Johnny's" If you guys know Mental Outlaw.) -these range in actors and targets.
Search Engines:
- Household Names (Google, Bing, Yahoo, etc)
- Advanced Operators ("Google Dorking")
- Network Mapping (nmap)
Target Research Tools:
Quick Disclaimer: I DO NOT ENDORSE USING ANY OF THESE TOOLS IN ORDER TO HACK, SCAM, OR EXPLOIT OTHERS FOR ILLEGAL AND UNETHICAL PURPOSES!!
- Shodan: Sentient hyper-optimized data access network. This tool has the ability to find the following: Device manufacturer names. IP addresses, software versions, locations, protocol-specific information. You can find out more about it with this article on Project SHINE
- "Dumpster Diving": "Old or unused device and documents often wind up in the dumpster or for resale online, Paper or electronic documents may have personally identifiable information."
- Port Scanning: NMAP and NETCAT- can detect all open ports- 65535 TCP and UDP ports, scans often check only the most commonly used ports, similar to recording where windows and doors are. It is similar to recording where all the windows and doors are - Noisy v Hidden.
- Vulnerability Scanning: After identifying the "windows and doors", look for unlocked ones. Can be performed by the same tools as port scanning.
Types of Cyber Attacks:
- Phishing: Social engineering scam, entices user to click malicious links, even with user training there is still a high probability of success, Spear phishing targets specific people or groups.
- Watering hole: Malicious actors predict a targets surfing habits, they infect vulnerable websites, and waits for the target to be infected.
- Keylogging: Records keystrokes and mouse inputs.
- Password attacks: Physical intrusion, Social engineering, fake login screens, bruteforce/rainbow tables, dictionary attack, intercepting, keylogging.
- Man-in-the-middle: Active Eavesdropping, Intercepts data sent. (Reconnaissance, Compromised credentials, altered data.)
- Code Injection: Inputs include database commands, text input locations, or HTML input fields, injections alter program flow or break it.
- Malware: Viruses, worms, trojans, bloatware/PUPs, Greyware.
- Data Exfiltration: Get data and run, common goal of industrial espionage or APTs, can be caught by firewalls and Intrusion Detection Systems looking for heavy traffic.
- Denial Of Service: Not focused on gaining unauthorized access, commonly utilizes botnets.
Risk Management
Definitions:
Components of risk - Vulnerability (Weakness)x Threat(invader) x Consequences(looting and piloting) = Risk.
Vulnerability - A flaw or weakness in a system that could be exercised (accidentally triggered or intentionally exploited) to result in a damaging action.
ICS Vulnerabilities- Reasons for increased vulnerability - Greater use of automation and inter-connectivity, Use of publicly accessible network infrastructure (telecommunications, Wireless, Internet)
This site from CISA has a whole catalog of known exploited ICS vulnerabilities!
Threat- A threat is the potential for a situation, method, or actor to successfully exploit a particular vulnerability (Human, Technical, Physical, Environmental, Operational).
Energy Sector Threat Landscape - Risks are real because threats are real, Asymmetric warfare is the norm, adversaries do not follow rules or regulatory checklists, open-source examples of attacker activities.
Consequence - A consequence is the damage that can result from a successful exploit. The consequence can include the loss of equipment, service, trust, and life.
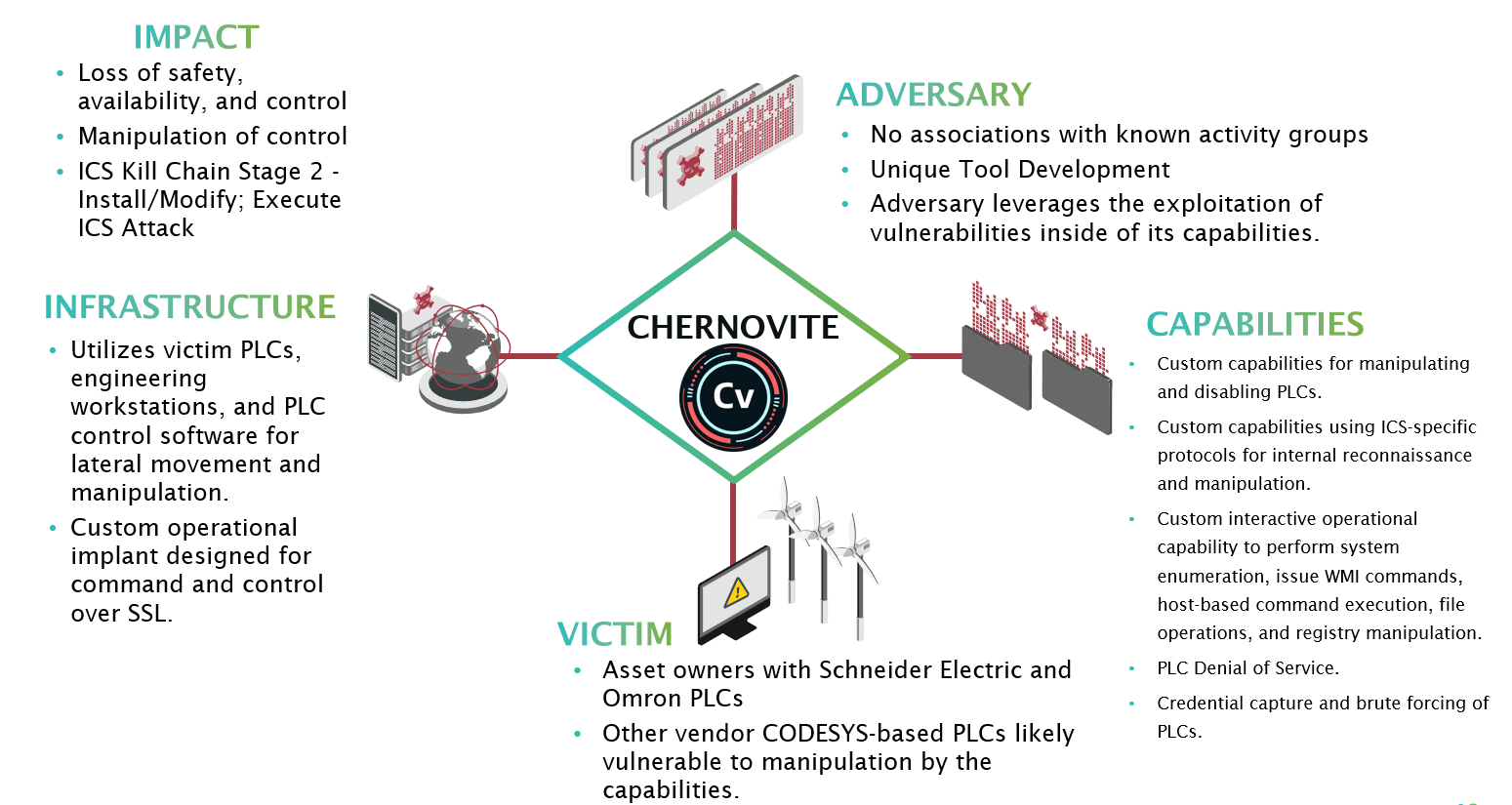
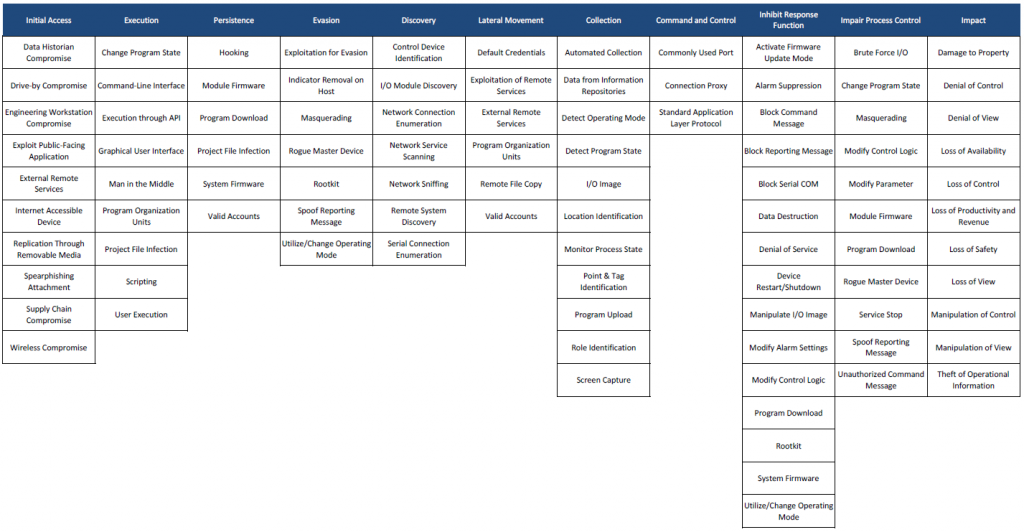
MITRE ATT&CK for ICS
Risk Calculation Example:
- Vulnerability= unsecured access to ICS x Threat=Professional hacker x Consequence = Loss of Life= High Risk.
- Vulnerability= Email access with easy to guess password x Threat=Adolescent x Consequence= Loss of Service= Medium Risk
- Vulnerability= No UPS or Surge protection x Threat=Flood x Consequence= Loss of Equipment= Low Risk
Applying Risk Management:
- Avoidance- Withdrawing from a risk scenario or deciding not to participate.
- Transfer- Risk is reduced or made more acceptable if it is shared.
- Mitigation- Risk reduction technique is applied to keep risk to an acceptable level and reduce the severity of loss.
- Acceptance- Risk is agreed, accepted, and accounted for.
Applying Risk Management to Previous Example:
- High access > Removal of remote access > New risk probability - Medium
- Medium Access > Change to secure password > New risk probability - Low
- Low Access > Replace Equipment > New risk probability- Low
Standards and Frameworks
Definitions:
Standard - Formal set of security requirements and measures that can be taken to meet those requirements.
Framework - Set of standards and best practices put together to help mission critical infrastructures.
Industry Standards and Frameworks- NIST Cybersecurity franework, ISA/IEC, 62443, CIS Critical Security Controls, ICS.
NIST CSF Core- Comprised of four elements - Functions, Categories, Subcategories, Informative References. 5 functions, 23 categories. 108 subcategories, 6 informative references.
NIST Cybersecurity Framework
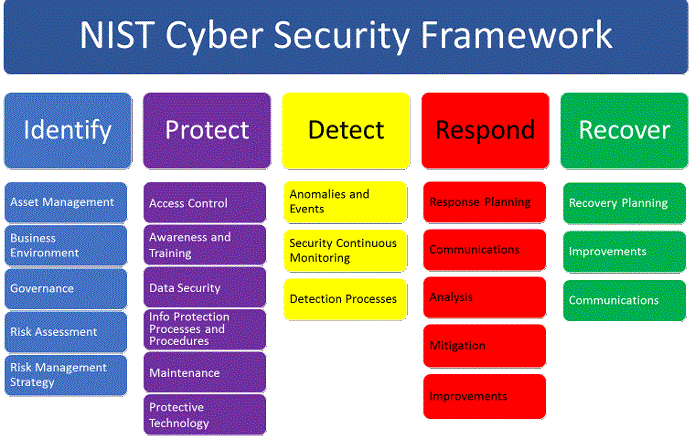
Definitions:
Function - Identify: System Baselines, Assessments, Cybersecurity Roadmaps, Security policy review and recommendations, consultancy services, Turnkey security solutions.
Function - Protect: Centralized access controls, Secure remote access, Physical security, Network solutions, Security hardening guides, Interconnection requirements, Whitelisting, Blacklisting.
Function- Detect: Asset management, Update management, Baseline monitoring, System health monitoring, Compliance, IDSs, SIEM systems, Training.
Function - Respond: Incident response and forensics, Alarms and alerts, Containment, Eradication, Recovery, Lessons learned.
Function - Recover: System recovery
ICS Cybersecurity Application

Definitions:
Security in Practice- Many methods exist for implementing elements of ICS Cybersecurity frameworks and standards discussed in previous sections. There is no one size fits all solution. Defense in-depth is a security approach that leverages a series of layered mechanisms to protect an organization from overall risk.
Industry Cybersecurity Difficulties- Use of unsecure protocols, Flat network layouts, Devices installed for 10+ years, Access controls spread across network, high patch management expense, Logging, alerting, monitoring, and forensics challenges, Automation without immediate oversight.
Cybersecurity tools - Unified threat management, Hypervisors (computer resources that can be divided to virtual machines), Software-designed networking, Security information and event management, anti-malware, System hardening, backup and recovery.
Cybersecurity Tools:
- OPNsense on SEL-3355: Next generation firewall with deep-packet inspection, Static and dynamic routing protocol support, IDS/IPS, High availability via CARP, IPSec VPN functionality that supports two factor authentication.
- ESXi Hypervisor: Bare-metal hypervisor, Efficient management software hat interacts directly with hardware.
- SEL-OTSDN- Control plane is abstracted from data plane and centralized in software controller, switch becomes a simple lookup table, Performance benefits for mission-critical applications. (Secure, fast healing, programmable, simple, interoperable, visible).
- SEL-751 and SEL-787 are industrial grade feeder protection relays, both feature local and centralized password management functionality, SEL 3620 Ethernet Security Gateway provides proxied access to relays.
- Security Onion: Open source network security platform that supports SELinux, Three Core functions (Intrusion detection, security monitoring, Log management). Built in tools.
- Symantec Endpoint Protection: Host-based anti-malware protection. Features include antivirus and antimalware.
- System Hardening using CIS benchmarks.
- SEL BaRT: Small, fast, portable OS backup tool, takes at least15 minutes. Portable (CD or USB utilization).
Summary
- OT Networks support operation of critical infrastructure
- Enterprise reference models inform secure industrial communication architecture.
- ICS networks face unique risks that must be assessed and managed appropriately.
- Industry standards organizations have created security guidelines and best practices for industrial cybersecurity such as the NIST ISF.
- There is tons of different software that apply to different risks and concepts.
- For the training lab of this presentation, we unlocked a three lock cylinder with lock-picking tools, which symbolizes the ease-of-access for some vulnerabilities in OT security, emphasizing that you should have more than one form of protection.
Final Thoughts and Extras
Ah... I'm finally getting to moving these blogs to my personal neocities! I'm so happy!! Please be sure to check out the rest of the blogs here:
